Abstract
HTTP 1.1 but with the following 4 improvements
- HTTP Multiplexing
- Server Push
- Compressing the HTTP Headers with HPACK
- HTTP messages are binary-encoded instead of ASCII-encoded, this is more efficient for parsing & less readable for hackers
HTTP Stream
- An HTTP stream consists of multiple HTTP Frame
Important
Each HTTP stream (a pair of HTTP Request/HTTP Response) doesn’t need to be sent in order in the same TCP Connection, so HTTP response can be received in a different order of sending the HTTP requests. This is achieved with HTTP Stream ID (流标示符) in the HTTP frame.
HTTP Frame
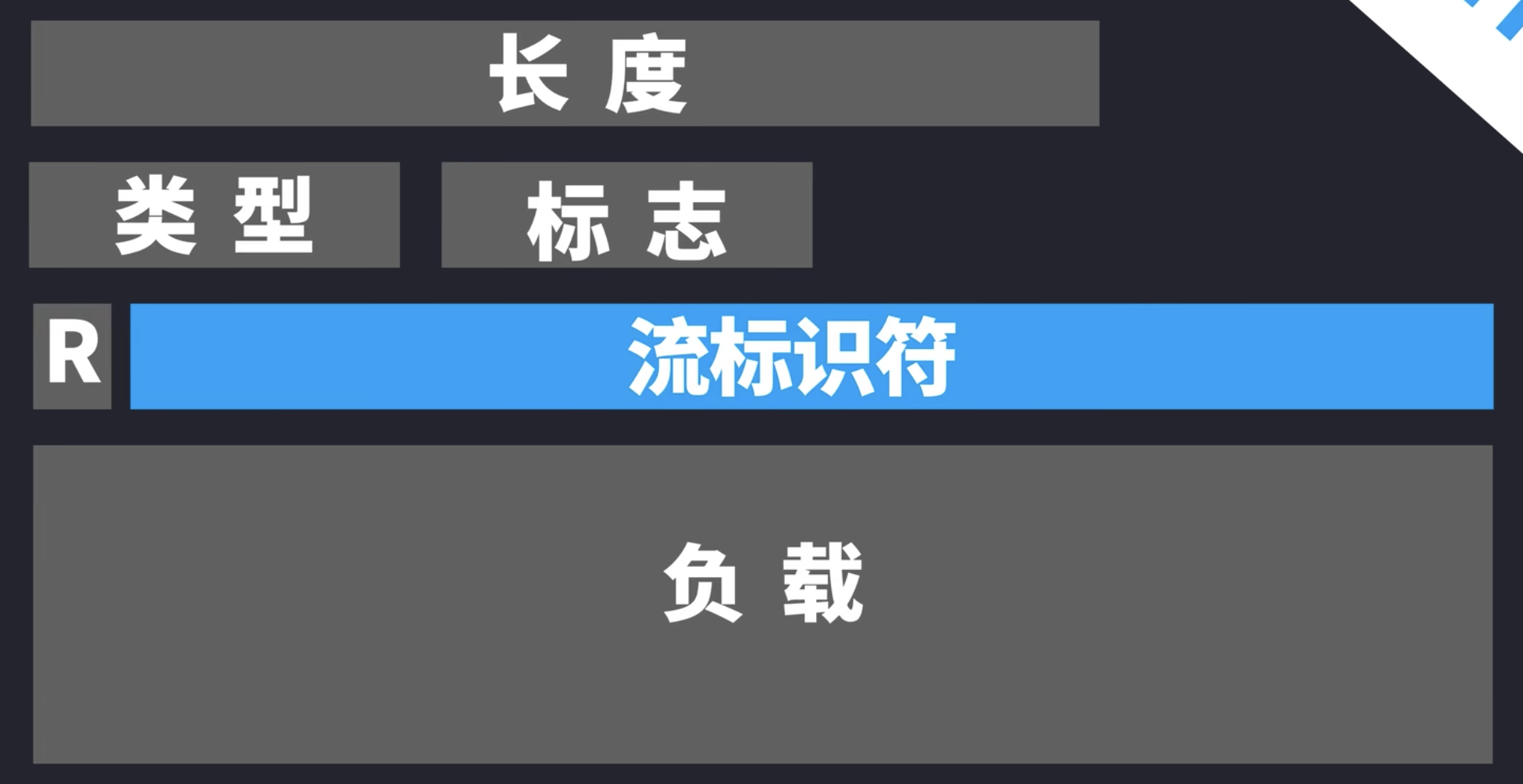
- An abstraction that allows us to divide HTTP Request and HTTP Response into multiple pieces
- There are two types - HTTP header frame, HTTP data frame
HTTP Multiplexing
- A HTTP 2.0 feature powered by HTTP Stream, solves HTTP Head-of-Line Blocking in HTTP 1.1. Each request-response pair is assigned a unique identifier (stream), allowing the client and server to send and receive responses out of order, independent of when the requests were made.
- Usually comes with TLS
Better performance
With multiple HTTP Request in one TCP Connection at the same time, waiting time reduced greatly aka better performance.
On high-loss or high-latency networks, HTTP/1.1 can actually be faster
Because we will still have the TCP Head-of-Line Blocking, and HTTP 1.1 may perform better with multiple TCP Connection.
To elaborate more, HTTP/2 multiplexes many requests over a single TCP connection. If one packet in that connection is lost, the entire connection stalls until retransmission happens. In contrast, HTTP/1.1 can open 6–8 parallel TCP connections per domain, so a packet loss only stalls that one stream, not all.
Server Push
- A HTTP 2.0 improvement that allows client/server to push Network Object it thinks client/server needs without the need to receive any specific HTTP Request for the object. This reduces the number of round trips taken
Caution
However, if a host clicks on the web page, many network objects will be received. This may result in potential DDoS: a single HTTP request can trigger multiple HTTP Response.
If not tuned carefully, the server might push unnecessary or already-cached resources, wasting bandwidth.
